Responding to a LogMeIn Phishing Scam
About The Project
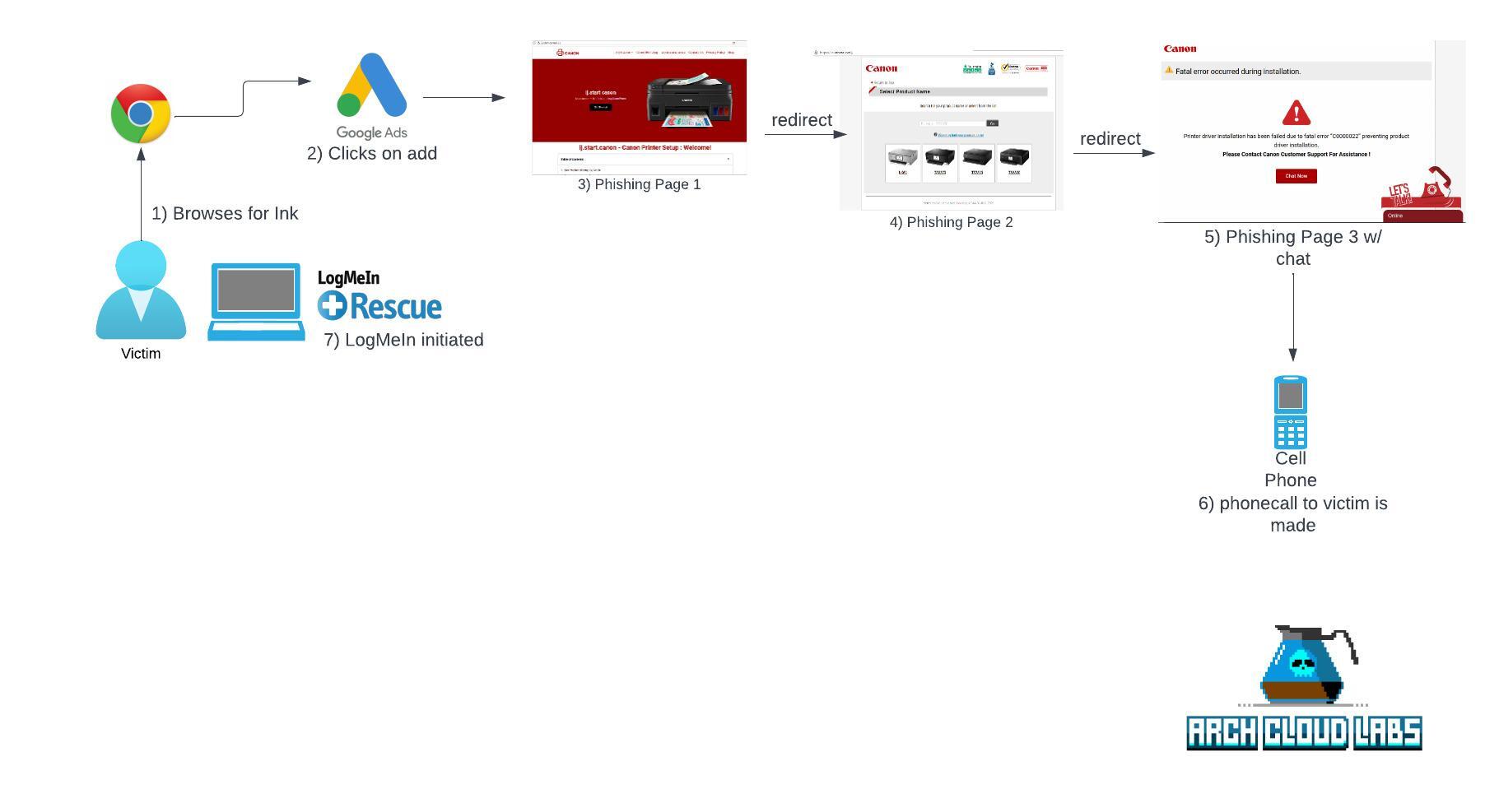
Recently a close friend fell victim to a scam that resulted in giving access to their laptop to a scammer via LogMeIn. This type of scam is inline with “refund scams” that YouTubers create videos for where they spend hours on call with the scammers to waste their time. This blog post will discuss the steps Arch Cloud Labs took post-access, the artifacts recovered and ultimately examining the phishing infrastructure. This blog post has been released with approval from the victim.
Initial Call
Obtaining relevant information to begin triage is critical for any incident response. Knowing the “who, what, where, why, when” can inform appropriate decision making steps to ensure no time is wasted during the beginning of an IR.
At 19:07 on March 25th, Arch Cloud Labs received the initial call stating access to a 3rd party was given to a friends laptop. A brief rundown of the events that took place prior to contacting them is as follows:
-
A new Canon printer was purchased, and there was difficulty installing drivers on Windows to get the printer to function.
-
Googling for Cannon printer drivers led them to a site that provided tech support.
-
After chatting online, an individual (the scammer) called the victim, prompted them to install LogMeIn and gained access to their machine.
-
While obtaining access, the scammer began running commands saying their computer was hacked and had viruses. The victim then disconnected the LogMeIn, and called Arch Cloud Labs.
Immediate questions include:
- When was access obtained (TODO: establish a timeline)
- What commands were run? (TODO: establish intent/motive)
- Was additional software installed? (TODO: stop the bleeding)
- Were any files stolen? (TODO: establish appropriate response procedures for the victim)
Upon obtaining access to the victim’s laptop, initial triage began to identify what the extend of damage was done. The following paragraphs breakdown answering these questions.
Beginning Triage
Upon obtaining access to the victim’s laptop, Sysinternals’ ProcExplorer was used to begin initial investigation into running processes to identify any anomalies. Windows Security settings were investigated to ensure nothing was disabled, and a virus scan via Microsoft Defender was initiated.
Next, ipconfig /displydns was executed to identify any DNS resolution still within the resolvers cache.
Unfortunately, this to did not return anything of value. Nor did examining common persistence locations such as RunKeys or startup folders.
These steps were to “stop the bleeding” should access still exist to the scammer through a different communication channel. Nothing immediately stood out, but a shortcut to LogmeIn was stored within Windows’ start menu.
Right clicking, and opening in the containing folder resolved to %APPDATA%\Local\ where the installation of LogMeIn exists. At this point, obtaining the file hashes via PowerShell of these installation files to verify this was the legitimate version of LogMeIn was achieved by submitting them to VirusTotal. The PowerShell command below obtains the hash for a given path.
$> get-filehash -Path C:\Path\Here -Algorithm SHA1
The file hashes returned to be the genuine versions of LogMeIn, and nothing is standing out as abnormal. However, its not clear what commands were executed by the scammer. Thankfully, there’s Windows Prefetch.
Windows Prefetch - Creating The Timeline & Hunting for File Access
The Prefetch directory located in C:\Windows\prefetch contains files about recently spawned processes.
The convention of this folder is <FILE STAMP> <UTILITY>.EXE-<ALPHA_NUMERIC>.pf.
Knowing the scammer logged in via LogMeIn, this process can be searched for to then establish a timeline of when LogMeIn was launched, and when Arch Cloud Labs obtained access to the machine.
Mar 25 18:54 LMI_RESCUERC.EXE-6080544A.pf
Mar 25 18:54 LMI_RESCUE_SRV.EXE-7259C5BB.pf
Mar 25 18:54 LMI_RESCUE_SRV.EXE-407C7717.pf
Mar 25 18:53 RUNDLL32.EXE-86454D92.pf
Mar 25 18:53 LMI_RESCUERC.EXE-D989BB66.pf
Mar 25 18:53 LMI_RESCUE.EXE-CCD2D2DD.pf
Mar 25 18:53 SUPPORT-LOGMEINRESCUE.EXE-81D36F99.pf <-- Initial access by the scammer obtained
LogMeIn Rescue is an enterprise support product to enable easy remote access solutions for enterprise IT. Given that LogMeIn Rescue is an enterprise product, one would assume a product key is being used. However, a free 14-day trial without a credit card is available on their official site, thus leading to the enterprise grade abuse.
Further examining the prefetch files listed below, a timeline begins to form where cmd.exe was spawned, tree was executed, and bcedit was opened. These handful of commands seem to simulate some type of work being done, playing to the narrative of the scammer that there is “malware on the victim’s machine”. This type of behavior is consistent with tech support scams, and refund scams.
Mar 25 19:00 LEDF11YY.B5E-FD08CD9F.pf
Mar 25 19:00 NETSH.EXE-59756CAC.pf <-- showing some IP information and claiming its "hackers"?
Mar 25 19:00 SVCHOST.EXE-B34B6FD4.pf
Mar 25 19:00 WMIAPSRV.EXE-CF150EEA.pf
Mar 25 19:00 DSONE.EXE-3166DEAF.pf <-- (DSOne being uninstalled)
Mar 25 18:59 DLLHOST.EXE-A432434E.pf
Mar 25 18:59 UN_A.EXE-094F1319.pf <-- (unrelated) Uninstaller for DSOne launching
Mar 25 18:59 CEFSHARP.BROWSERSUBPROCESS.EX-28BB303F.pf
Mar 25 18:59 CEFSHARP.BROWSERSUBPROCESS.EX-28BB3045.pf
Mar 25 18:59 DSONESHUTDOWN.EXE-6834F023.pf <-- (unrelated) Uninstalling Driver Support One (DSONE)
Mar 25 18:59 UNINSTALL.EXE-B30DD53C.pf <-- (unrelated) Uninstalling Driver Support One (DSONE)
Mar 25 18:57 CMD.EXE-2EB3E6E2.pf
Mar 25 18:57 BCDEDIT.EXE-EB47CDA5.pf <-- popping open bcedit
Mar 25 18:57 DLLHOST.EXE-B20B2F7A.pf
Mar 25 18:56 TREE.COM-3A12A283.pf <-- running tree
Mar 25 18:56 CMD.EXE-CD245F9E.pf <-- cmd.exe
Mar 25 18:56 DLLHOST.EXE-CDDFFDB0.pf
Mar 25 18:55 SVCHOST.EXE-7218DCB2.pf
Mar 25 18:55 CONTROL.EXE-5BCB0217.pf <-- Opening control panel
Upon reviewing the prefetch artifacts, a timeline has been established for when the scammer had access to the machine to when they initially gained access to when Arch Cloud Labs gained access to the machine. At this point in the investigation this puts our time frame from 18:55 to 19:07.
With a timeline established, I began examining file timestamp attributes to identify if anything had been accessed by the scammer. The PowerShell one-liner below will list the last access time for a given path.
$> get-childitems -recursive | select LastAccessTime,FullPathName
The example image below demonstrates the output of this command, but on a test virtual machine as to not reveal sensitive data from a victim’s machine.
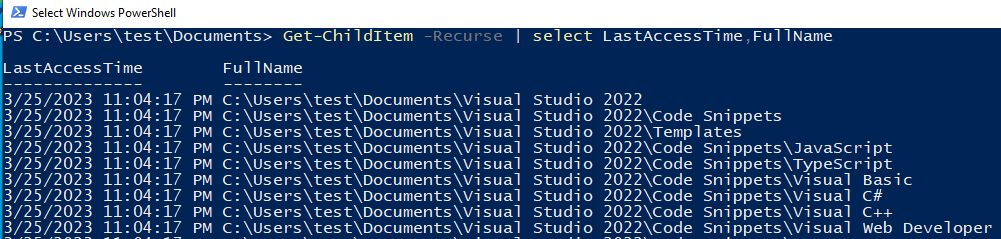
The result of this command on the victim’s machine resulted in no files identified as being accessed. At this point in the investigation, virus scans, timelining, and live triage revealed enough information to start moving the victim into response mode, and have them begin changing passwords for their accounts.
Now, examining the phishing infrastructure that led to this in the first place could begin.
Phishing Pages Leading to 1:1 Chat
The victim’s browser history still contained links to the original phishing pages. Backtracking through these pages resulted in discovering a Google ad which initially led the victim to believe they were going to a legitimate Canon printer website to obtain printer drivers.
The initial ad took them to “ij-start-cannon[.]us” shown in the image below. This website acts as the landing page for victims to choose “get started” leading them to the second phishing domain.
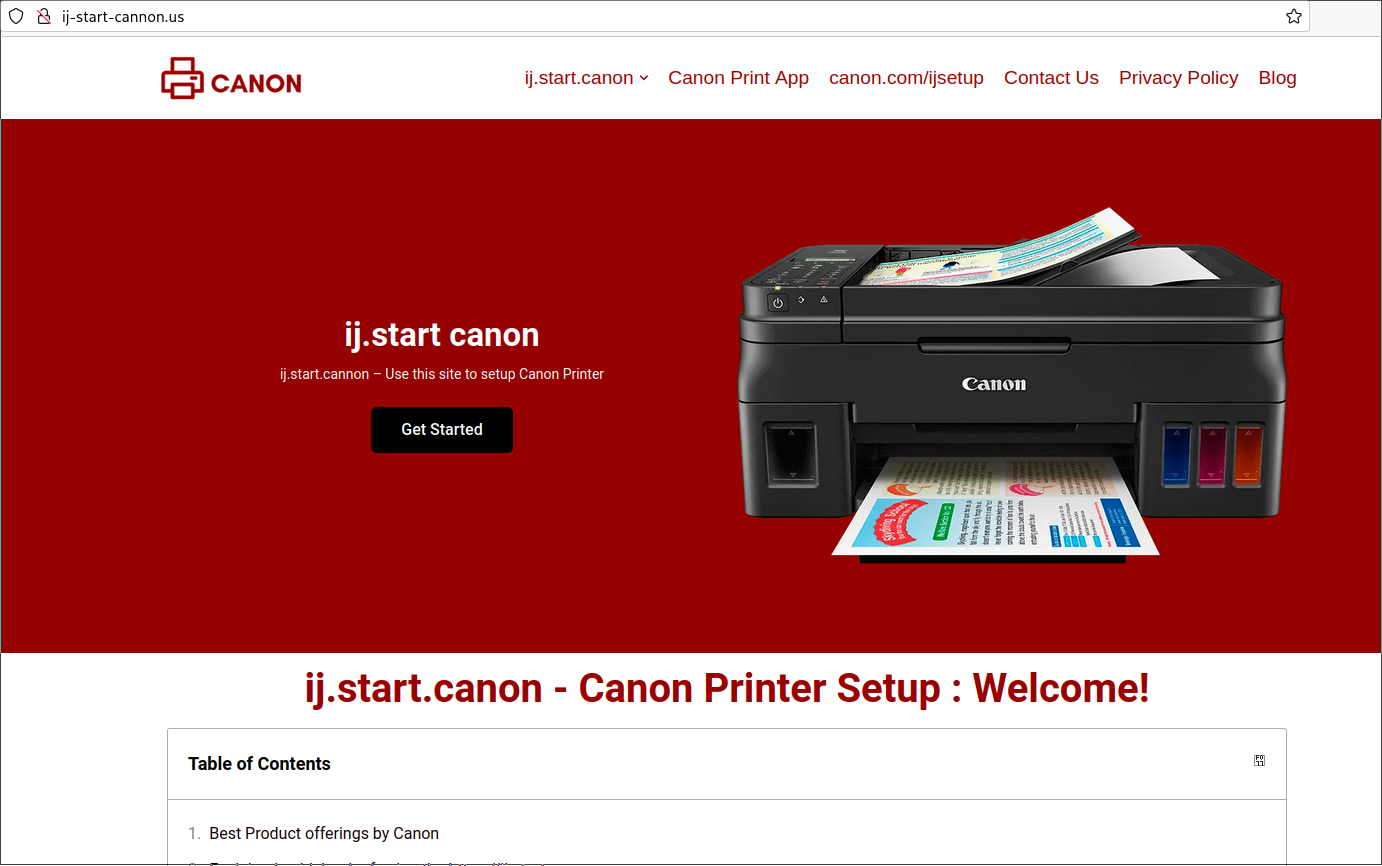
Upon selecting “Get Started”, the victim is redirected to a second website (ca-canoss.xyz/ij) to select their product and ultimately download drivers.
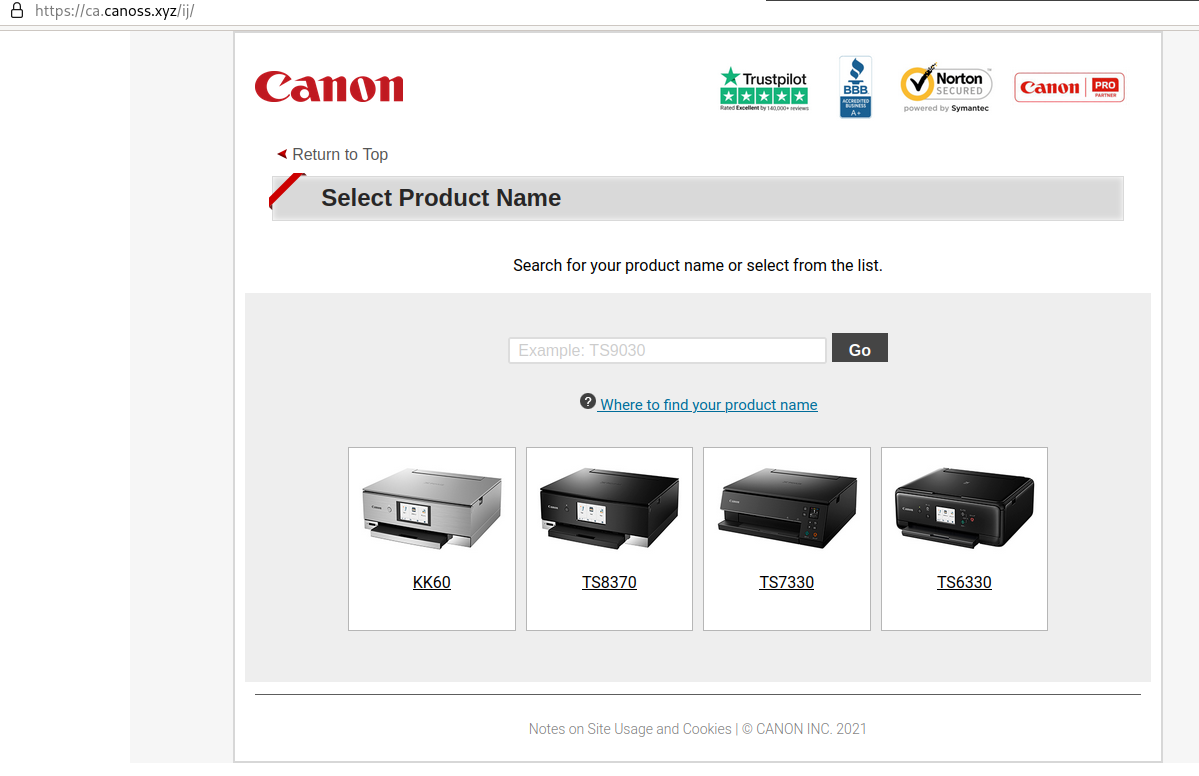
The preivous two phishing pages have taken the time to look legitimate, but are barely configured Wordpress sites. By navigating to the root of the domain, no redirects exist, thus revealing the default Wordpress blog.
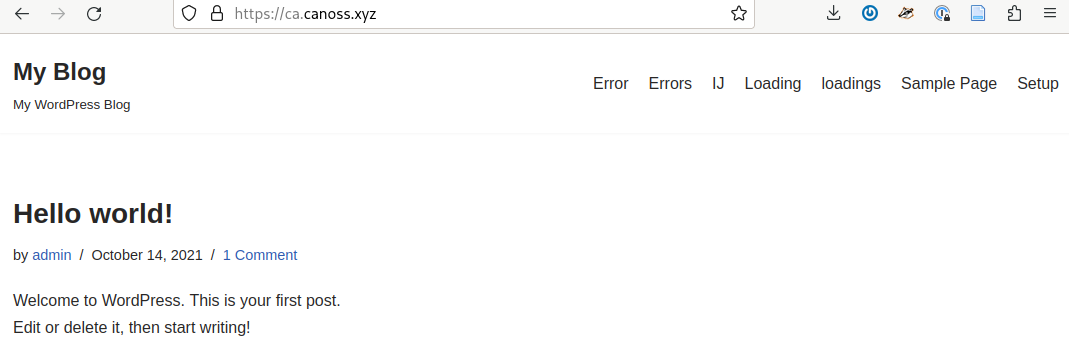
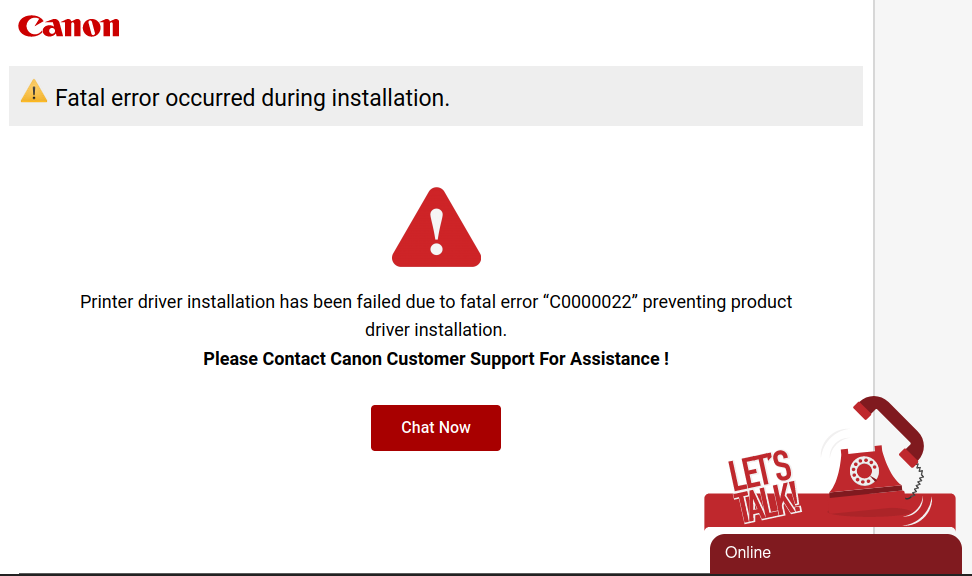
Next, the victim chooses their setup instructions to get redirected to a separate page on the same domain. Regardless of their choice, they end up at the same error page on a 3rd domain of canen[.]ink.
This domain which has them chat with a online representative in order to then chat on the phone. Once on the phone the scammer will instruct how to enable remote access so they can “help” the victim.
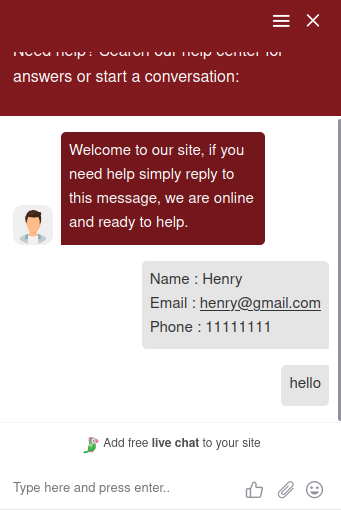
At this point the chat menu prompts the victim for a phone number, e-mail address and name to begin communication.
Digging into Domains
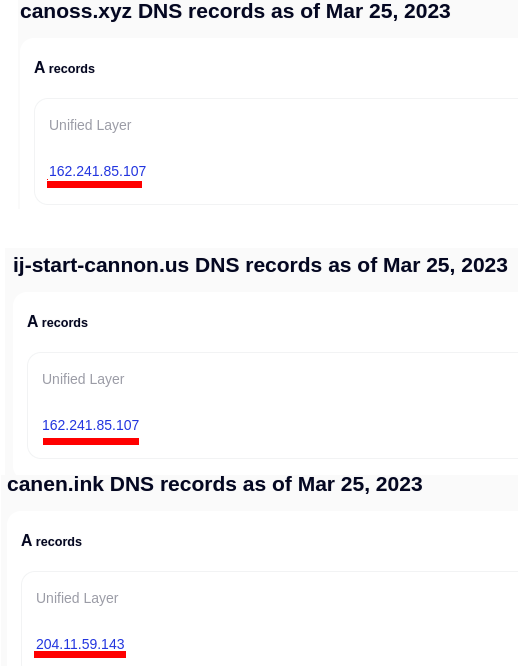
Security Trails offers historial DNS data which revealed two of these three domains being hosted at the same IP address and all three being hosted by the same provider “Unified Layer”. Unified Layer offers managed Wordpress hosting which is exactly what these scammers are taking advantage of in their numerous registered domains discussed below. At this point in time, Arch Cloud Labs has contacted Unified Layer support with said phishing domains.
Pivoting on these domains in VirusTotal, they all came back benign. The TLS certificate for canen[.].ink was just registered two days ago (March 23rd) at the time of this blog. This infrastructure was caught early and likely explains the misconfiguration of the Wordpress sites.
Numerous other domains are hosted currently at the 162[.]241[.]85[.]107 IP address from Unified Layer which are also phishing related. Examining the byomkeshbakshi[.]me domain revealed a page hosted on Github Pages.
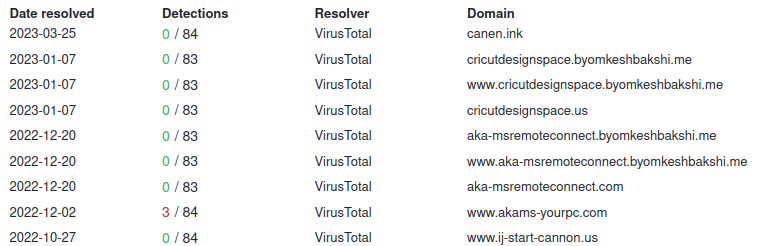
Linking A Domain to a Github Account
One of the strager things about these domains are the historical ties to a “byomkeshbakshi.me” domain. Per Wikipedia:
“Byomkesh Bakshi is an Indian-Bengali fictional detective created by Sharadindu Bandyopadhyay. Referring to himself as a “truth-seeker” or Satyanweshi in the stories, Bakshi is known for his proficiency with observation, logical reasoning, and forensic science which he uses to solve complicated cases, usually murders, occurring in Calcutta.
Is this some odd subtle nod to digital forensic examiners? who knows, but an interesting discovery none the less. Referencing this domain within Security Trails revealed 192 enties, most of which were related to Unified Layer’s CPanel for managed Wordpress. However, all of the legitimate subdomains were names of popular entertainment companies, social media websites or sports websites. These results can be viewed here.
An intersting discovery was a Gitub Account with the name “wwwakamsyourpc”. This Github name matches not only a domain discovered in the SecurityTrails data (akams-yourpc[.]byomkeshbakshi.me), but also the same content hosted on a Github IO pages is also being hosted at akams-yourpc[.]com on the same IP as canon domains at 162[.]241[.]85[.]107. Unfortunately at this time there’s no substantial data within said Github account to uncover further content.
Following the links on akams-yourpc, ultimately result in a Minecract phsihing page attempting to get you to log into your Microsoft account.
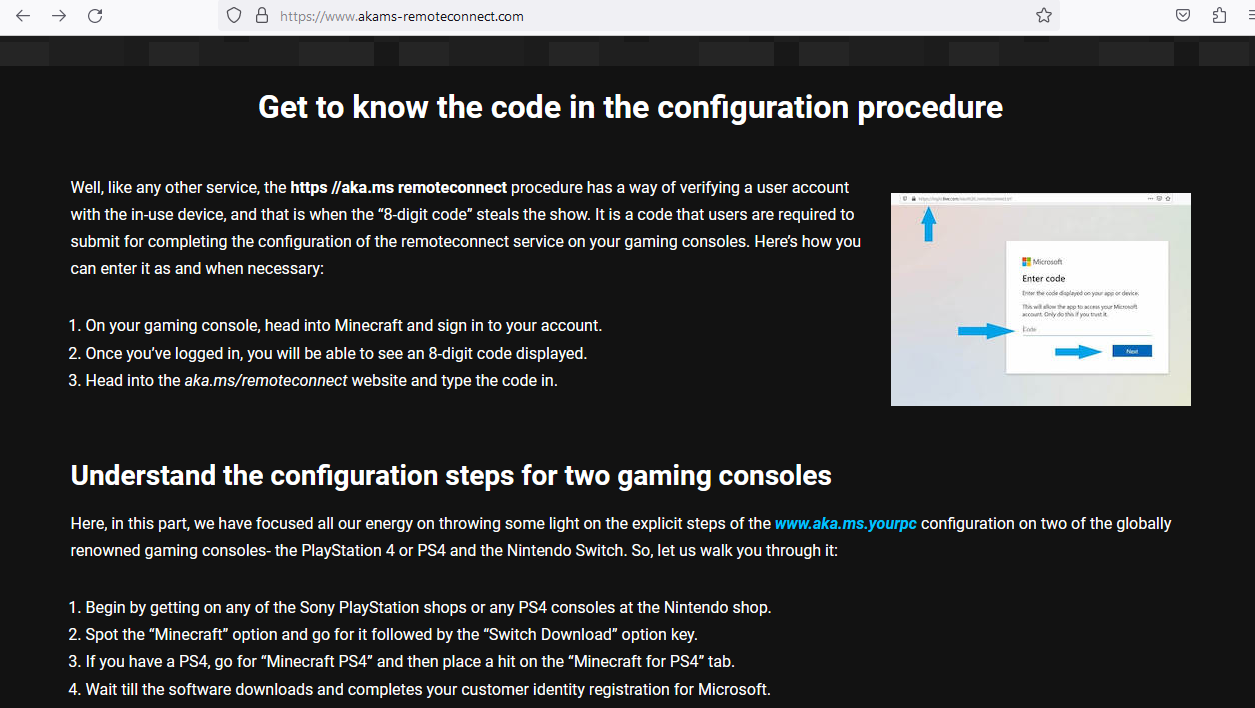
Disclaimer in the Wordpress Sites & DMCA Protection?
Each one of these Wordpress sites had a disclaimer at the bottom stating they were not affiliated with the brand they were impersonating. Perhaps the scammer thinks this makes them adverse to takedowns?
Interestingly enough, the original landing page has applied for DMCA protection and is registered on the DMCA website.
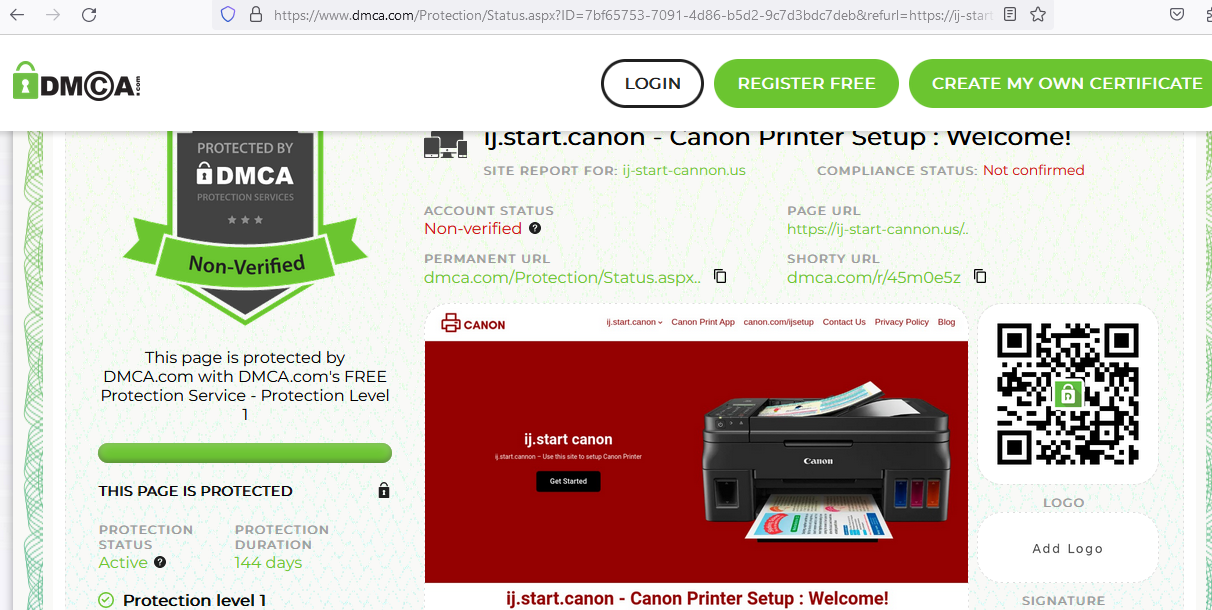
Per the DMCA protection act, the audio, video, images, etc… on this site are considered intellecutal property of the owner. This is hilarious, and you can view it at the real DMCA website at https://[.]dmca.com/r/45m0e5z
Conclusion
Arch Cloud Labs speculates with medium confidence this was most likely an IT Help desk scam. The information obtained from examining the domains in combination with the misconfigured Wordpress sites, and lack of post-exploitation activity on the laptop performed suggests the intent was to scare the user into paying for said “services”. It is unclear at this time how the scammer would of requested money (credit card/cryptocurrency/money order/amazon gift cards/etc).
These types of scams are not new, but they’re still relevants because they work. Talk to your loved ones about these scams, and what to do if they encounter themselves in this situation. Just like an enterprise organization has an incident response plan for their infrastructure, you should have one for your family.
Thank you for reading, if you enjoyed this, consider sharing!
IoCs
https://securitytrails.com/list/apex_domain/byomkeshbakshi.me
ij-start-cannon[.]us
canoss[.]xyz
byomkeshbakshi[.]me
akams-yourpc[.]com
aka.ms.yourpc[.]com
akams-remoteconnect[.]com
canen[.]ink
cricutdesignspace[.]byomkeshbakshi[.]me
www[.]cricutdesignspace[.]byomkeshbakshi[.]me
cricutdesignspace[.]us
aka-msremoteconnect[.]byomkeshbakshi[.]me
www[.]aka-msremoteconnect[.]byomkeshbakshi[.]me
aka-msremoteconnect[.]com
www[.]akams-yourpc[.]com
www[.]ij-start-cannon[.]us
www[.]f[.]adoss[.]xyz
f[.]adoss[.]xyz
sam[.]adslock[.]xyz
www[.]sam[.]adslock[.]xyz
autodiscover[.]fmoviess-to[.]com
webmail[.]fmoviessto[.]com
cpcalendars[.]fmoviessto[.]com
fmoviess-to[.]com
fmoviess-to[.]byomkeshbakshi[.]me
cpcontacts[.]fmoviess-to[.]com
www[.]fmoviessto[.]com
www[.]fmoviess-to[.]com
www[.]fmoviessto[.]byomkeshbakshi[.]me
webdisk[.]fmoviessto[.]com
webdisk[.]fmoviess-to[.]com
cpanel[.]fmoviessto[.]com
cpanel[.]fmoviess-to[.]com
autodiscover[.]fmoviessto[.]com
mail[.]fmoviess-to[.]com
www[.]fmoviess-to[.]byomkeshbakshi[.]me
cpcontacts[.]fmoviessto[.]com
fmoviessto[.]com
cpcalendars[.]fmoviess-to[.]com
fmoviessto[.]byomkeshbakshi[.]me
webmail[.]fmoviess-to[.]com
mail[.]fmoviessto[.]com
akams-yourpc[.]byomkeshbakshi[.]me
www[.]akams-yourpc[.]byomkeshbakshi[.]me
akams-yourpc[.]com
ij-start-connon[.]us
ij-start-cannon[.]byomkeshbakshi[.]me
ij-start-connon[.]byomkeshbakshi[.]me
ij-start-cannon[.]us
www[.]ij-start-cannon[.]byomkeshbakshi[.]me
www[.]ij-start-connon[.]byomkeshbakshi[.]me
webdisk[.]tubitv-activates[.]com
autodiscover[.]tubitv-activates[.]com
cpcalendars[.]tubitv-activates[.]com
mail[.]tubitv-activates[.]com
webmail[.]tubitv-activates[.]com
cpanel[.]tubitv-activates[.]com
cpcontacts[.]tubitv-activates[.]com
www[.]tubitv-activates[.]com
nba-streams-reddit[.]byomkeshbakshi[.]me
tubitv-activates[.]byomkeshbakshi[.]me
tubitv-activates[.]com
nba-streams-reddit[.]com
www[.]tubitv-activates[.]byomkeshbakshi[.]me
www[.]nba-streams-reddit[.]byomkeshbakshi[.]me
autodiscover[.]pelisplus1[.]com[.]mx
webmail[.]pelisplus1[.]com[.]mx
cpcontacts[.]pelisplus1[.]com[.]mx